The internet has become an integral part of our lives. We rely on it for communication, entertainment, education, business, and more. However, with great connectivity comes privacy and security concerns. That’s where proxies come in. Proxies act as intermediaries between you and the internet, helping protect your identity and information.
There are two main types of proxies – transparent and non-transparent. While both offer benefits, there are some key differences you should understand before choosing one over the other. This comprehensive guide will provide an in-depth look at the difference between transparent proxies and non-transparent proxies to help you determine which is better for your needs.
What is a Proxy Server?
Before diving into the specifics of transparent and non-transparent proxies, let’s take a step back and define what a proxy server is exactly.
A proxy server acts as an intermediary between your computer and the wider internet. When you connect through a proxy server, internet requests from your computer are first routed through that server. The proxy evaluates the request, performs any configured processing, then forwards the request on to the destination server while masking your computer’s IP address.

The destination server responds as normal, returning the requested content to the proxy server. The proxy then delivers the content back to your computer. This routing through an intermediary server provides a layer of anonymity and can allow you to bypass censorship or geographic restrictions on content.
Some key benefits of using a proxy server include:
- Anonymity – Your originating IP address is hidden from destination servers
- Location spoofing – Proxies allow you to appear to be connecting from a different geographic location
- Extra security – Proxies provide an additional layer between your device and the open internet
- Circumventing restrictions – Proxies can be used to bypass censorship or access content blocked in certain regions
Now let’s look at how transparent and non-transparent proxies differ.
Transparent Proxy
A transparent proxy reveals its existence to both the client (your computer) and destination server. Your system is aware you are connecting through a proxy, and the proxy identifies itself to remote servers when forwarding requests.
Some key features of transparent proxies:
- Your IP address is replaced with the proxy’s IP address when communicating with destination servers. This hides your originating location while allowing the proxy server to be identified.
- No manual proxy configuration is required on your local system. Redirection through the transparent proxy happens automatically based on network settings.
- All internet traffic is routed through the proxy. Specific sites or protocols cannot be excluded.
- URL requests are not encrypted between your system and the proxy. Your web activity may be logged and monitored.
- Generally used for content filtering, access control, and traffic analytics. User anonymity is not a priority.
Transparent proxies are commonly deployed by schools, businesses, ISPs, and governments to monitor user activity and restrict access to prohibited content. For example, a school might use a transparent proxy to block inappropriate websites or limit bandwidth-heavy streaming traffic.
Non-Transparent Proxy
A non-transparent proxy conceals itself from the requesting client and destination servers. Neither your computer nor remote sites are directly aware you are connecting via a proxy.
Some key features of non-transparent proxies:
- Both your IP address and the proxy’s IP address are hidden from destination servers. All traffic appears to originate from the proxy.
- Manual proxy configuration is required on your local machine to route connections through the non-transparent server. Traffic is not redirected automatically.
- You can selectively route only certain traffic through the proxy, allowing direct internet access for everything else.
- Communication between your system and proxy is encrypted end-to-end. Sites cannot monitor your activity.
- Used when user privacy and anonymity are critical. Does not usually involve content filtering or access controls.
Non-transparent proxies are more common among privacy tools and services aiming to hide users’ identities and evade surveillance. For example, the Tor anonymity network utilizes a series of encrypted non-transparent proxies to conceal users’ originating locations and usage patterns.
The Differences Between Transparent and Non-Transparent Proxies

To summarize, some of the main differences between transparent and non-transparent proxy servers:
- Visibility – Transparent proxies reveal themselves to both the user and destination sites while non-transparent proxies conceal themselves from everyone.
- Configuration – Transparent proxies do not require any special configuration while non-transparent proxies need manual setup on the client side.
- Routing – Transparent proxies intercept all traffic automatically whereas non-transparent proxies only apply to selectively routed connections.
- Encryption – Communication with non-transparent proxies is encrypted end-to-end. Transparent proxy connections are unencrypted.
- Anonymity – Non-transparent proxies prioritize hiding user identities. Transparent proxies focus more on content controls than anonymity.
- Use cases – Transparent proxies are favored in schools and businesses for monitoring and access restrictions. Non-transparent proxies are preferred by users who value privacy.
The following chart summarizes some of these key variances:
| Feature | Transparent Proxy | Non-Transparent Proxy |
|---|---|---|
| Visibility | Proxy reveals itself | Proxy is concealed |
| Client configuration | Not required | Manual setup required |
| Routing | All traffic routed through proxy | Selective routing only |
| Encryption | No encryption | End-to-end encryption |
| Anonymity | Low priority | High priority |
| Use cases | Content filtering, access controls | User privacy, anonymity |
Understanding where transparent and non-transparent proxies overlap and diverge will help guide you in choosing the right proxy solution for your needs.
How Does a Transparent Proxy Work?
Now that you know the basics, let’s take a deeper look at how transparent proxies function under the hood.
A transparent proxy is generally implemented at the network perimeter. It could be at an organization’s internet gateway, on an internal network node, or at an ISP’s infrastructure. The proxy has its own public IP address and full two-way connectivity to internet sites and services.
Client systems are configured to point at the transparent proxy as their default gateway for internet traffic. This can be done manually by setting the proxy’s IP as the default gateway address on each device. More often, the proxy IP is automatically assigned to clients as the default route by network DHCP or IP configuration settings.
With the proxy set as the gateway, all outbound traffic from clients is unconditionally routed through the transparent proxy without any client involvement. The proxy accepts these incoming connections, replaces the internal client IP address with its own public IP, then opens a secondary connection to the destination site and relays traffic bidirectionally.
When the destination server responds to requests, it does so by communicating directly with the proxy’s IP address. The proxy forwards responses back to the appropriate client based on details like the client’s port number included in each packet.
This gateway configuration allows all client-to-internet traffic to be funnelled through the transparent proxy for monitoring, filtering, and analysis purposes. However, the client’s IP is still ultimately revealed to destination sites to allow normal two-way communication. Clients also have unencrypted connections with the proxy, allowing the proxy to log activity.
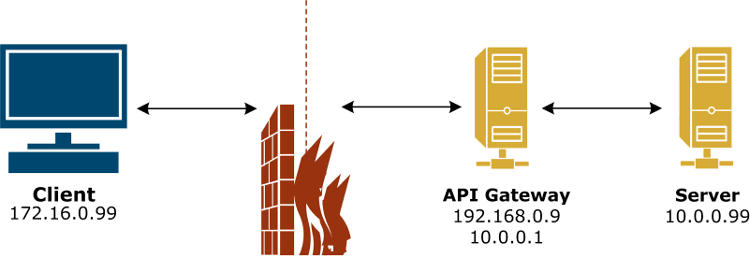
Transparent proxy sitting between client and server
Common use cases for transparent proxies include:
- Filtering – Block malware, censor web content, limit bandwidth-heavy activities like video streaming
- Access controls – Limit which sites or protocols employees can use based on HR policies
- Logging and reporting – Monitor employee internet usage patterns and traffic analytics
- Caching – Speed up common requests by caching content at the proxy layer
While providing some security and management benefits, the visibility and lack of encryption mean transparent proxies do not offer true anonymity. Non-transparent proxies are better suited for that goal.
How Does a Non-Transparent Proxy Work?
In contrast to transparent proxies, non-transparent proxies require clients to deliberately route traffic through them, and they conceal themselves from destination servers. This offers much greater privacy and anonymity.
Users must manually configure their internet clients like web browsers to use the non-transparent proxy. This means setting the proxy server IP address and port in the client’s network settings. The client can then selectively route traffic through this proxy based on user-defined patterns and filters. All other traffic is sent directly from the client to destination servers without passing through the proxy.
When a connection does get routed through the non-transparent proxy, the process is as follows:
- The client encrypts the request destined for the external server and sends it through an encrypted tunnel to the proxy server. This tunnel shields traffic from surveillance and hides the user’s IP address.
- The proxy accepts the encrypted request, decrypts it, then opens its own separate encrypted session with the requested site to forward the request.
- Responses from the destination server travel back through this encrypted proxy channel. The proxy encrypts the responses and relays them through the secure tunnel back to the originating client.
This workflow maintains end-to-end encryption between the client and proxy while also keeping the proxy’s own IP hidden from destination sites. All external servers see is traffic coming from the non-transparent proxy’s IP, with no direct interaction with or visibility into the user initiating the requests.!

Non-transparent proxy using encrypted tunnels
Common use cases for non-transparent proxies revolve around anonymity and evading surveillance, such as:
- Encrypted web browsing to prevent snooping on traffic
- Masking your geographic location and usage patterns
- Bypassing IP-based blocks and blacklists
- Anonymous file sharing and torrenting
- Circumventing censorship to access blocked content
For maximum anonymity, chains of multiple non-transparent proxies can be used to create an encrypted tunnel through several intermediaries. This prevents any single proxy from being able to monitor user activity or trace traffic back to its origin.
Which Type of Proxy is Better?
With an understanding of how each type of proxy works, which should you choose for your needs?
As with most technology decisions, the “best” option depends on your specific use case and priorities. Here are some guidelines:
- If you need to monitor and filter web activity, a transparent proxy is likely the better fit. IT departments commonly deploy transparent proxies to analyze employee internet usage patterns and limit access to prohibited content or sites.
- If user privacy is your top priority, a non-transparent proxy is preferred. Individuals concerned about anonymity online often route their traffic through encrypted non-transparent proxies to mask their digital footprint.
- If you want location spoofing capabilities, both proxy types allow this. Connecting from a different geographic region can be helpful for accessing geo-restricted content.
- If you’re trying to circumvent censorship, non-transparent proxies offer more reliable and secure access to blocked content and sites.
- If you need to proxy only some of your traffic, non-transparent setups provide selective routing while transparent proxies require funneling all traffic through them.
- If you have limited technical expertise, transparent proxies are easier to deploy as they don’t involve manual client configurations. Non-transparent proxies require more effort to set up correctly.
Additionally, here are some general advantages of each proxy type:
Benefits of transparent proxies:
- Easier implementation without end-user involvement
- All traffic is necessarily routed through proxy
- Support content filtering, access controls and traffic analytics
- Allow blocklisting known bad IP addresses
- Can cache content to improve performance
Benefits of non-transparent proxies:
- Stronger anonymity and privacy protection
- Encrypted tunnels prevent surveillance
- Selectively route only traffic you want proxied
- Chain multiple proxies for maximum anonymity
- Better circumvention of censorship
- Users have full control over routing decisions
To recap, transparent proxies excel at content filtering for organizations while non-transparent proxies better serve users prioritizing privacy and anonymity. Consider your own motivations and constraints to determine the right solution.
Both proxy types have their merits, and the choice ultimately depends on your specific use case. Evaluate your priorities around visibility, encryption, routing control, and implementation complexity to select if a transparent or non-transparent proxy better fulfills your needs.
Implementing Transparent Proxy Solutions
If after reviewing the differences you’ve decided a transparent proxy aligns with your goals, how do you go about setting one up?
While individuals can configure basic transparent proxies for personal use, large-scale implementations are typically deployed by network administrators within organizations or ISPs. Here are some best practices for rolling out a transparent proxy:
Choose a suitable proxy server software
There are many open source and commercial proxy server platforms available. Common options include Squid, Varnish, HAProxy, Nginx, and proprietary hardware proxies. Consider factors like performance, features, and ease of management.
For transparent proxying, the software must support intercepting connections based on routing rules and IP tables. NAT for hiding client IPs is also required.
Locate the proxy strategically
The proxy should reside between internal clients and your external internet gateway to intercept all WAN traffic. For maximum efficiency, implement the proxy on fast and robust hardware.
Configure NAT and default gateway routing
Clients must have their default gateway set to the proxy’s internal IP rather than the actual internet gateway. The proxy replaces the internal IP with its own public IP using IP masquerading.
Define filtering rules
Configure content and protocol filters based on your policy objectives, such as banning certain websites or blocking file sharing traffic.
Authenticate clients
For greater visibility into who is generating traffic, require user or machine credentials to authenticate clients through the proxy.
Monitor performance
Watch for bottlenecks or slowdowns caused by the proxy and tune resources accordingly. Caching and other optimizations can also help improve speed.
Log and analyze activity
Recording proxy access logs allows you to generate reports on things like sites visited and bandwidth usage patterns.
With appropriate planning and configuration, a transparent proxy can provide significant policy enforcement, security, and traffic management benefits. The implementation steps above provide a starting point for maximizing your transparent proxy’s effectiveness.
Implementing Non-Transparent Proxy Solutions
If your needs favor the privacy-preserving approach of a non-transparent proxy, how should you go about setting one up?
Implementing a non-transparent proxy involves two key steps – configuring the actual proxy server, and then setting up clients to route traffic through it.
Select and configure a non-transparent proxy server
Numerous commercial, free, and open source proxy servers exist like Squid and Shadowsocks. The server should have these features:
- Non-transparent mode allowing IP obfuscation
- Encryption support using protocols like SSL or TLS
- Port forwarding to relay client connections
- Rules to selectively route clients’ proxied traffic
The server can reside on your own hardware or hosted externally through a provider. For anonymity, use hosts outside the jurisdiction you want to evade.
Configure clients to use the proxy
Configure web browsers, torrent clients, or other internet-enabled apps on user devices to funnel traffic through the non-transparent proxy.
Most clients have settings to manually enter the proxy’s IP address, port, and parameters like encrypted vs unencrypted connections. Wildcard filters can be defined to determine which traffic gets proxied.
The clients handle encrypting data and opening secure channels to the proxy. Apps will typically let you set multiple proxies and toggle them on and off as needed.
With clients configured to selectively route traffic through one or more non-transparent intermediaries, you establish an encrypted tunnel from endpoint to endpoint with masking of both your location and proxy IP destination. This provides the anonymity benefits associated with proxies while still allowing direct unproxied internet access as desired. Careful configuration is important, but ultimately gives you flexibility and privacy.
Conclusion
Determining if a transparent or non-transparent proxy is right for you depends on your priorities and constraints. Evaluating factors like visibility, routing control, and implementation difficulty for your specific use case makes the better option clear.
Transparent proxies excel at content filtering through easy deployment on internal networks but provide minimal anonymity. Non-transparent proxies demand more effort to configure but offer strong privacy preserving features like encrypted tunnels.
Understanding the core differences allows you to tailor your proxy solution to your intended goals, be it anonymous browsing, securing remote access, bypassing geographic restrictions, or simply gaining greater visibility into network activity.
With the comprehensive information provided in this guide, you should now have clarity on selecting between proxy transparency types. By choosing the one suited to your particular needs and setting it up properly, a proxy can be a versatile tool improving internet security, privacy, and access.



